MIKELANGELO is targeting to develop hypervisor-level security mechanisms for monitoring and mitigating cache side-channel attacks. Such attacks have been shown to allow an attacker operating from within a VM to extract sensitive information from a co-located VM, via meticulous manipulation of its own memory access, which induces specific patterns of last-level cache (LLC) hit-miss behavior on the shared processor. This, in turn, allows it to deduce information about the activity of the co-located VM.
There are currently a multitude of mechanisms in various layers which aim at mitigating and reducing the cache attack-surface. However, these mechanisms tend to either be implemented at the application level (e.g., as specific patches to crypto libraries), or at the hardware level (e.g., isolating LLC sections for a specific VM). Our vision is developing enhancements to the hypervisor so as to obliterate such attacks. You can call it SCAM (side-channel attack mitigation). We know we do. Our focus on hardening the hypervisor stems from our dual view of things: (1) security should not depend on whether or not every application developer is also a security expert, and as such has installed measures to defend against such attacks, and (2) security should not depend on the specific hardware on which the VM is running. The hypervisor-level is the agnostic-level which should provide security measures in such scenarios.
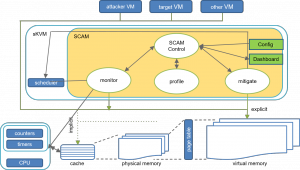
The basic architecture underlying our solutions is based on user-level processes interacting to provide a complete suite of mechanisms, including monitoring, profiling, and mitigation.
Figure: SCAM’s architecture in a glance
MIKELANGELO envisions several security mechanisms as part of its hardening of KVM, to be incorporated in the project sKVM hypervisor, including:
- Monitoring and identifying potentially malicious activity by analyzing system counters and timers
- Introducing well-targeted noise into cache activity
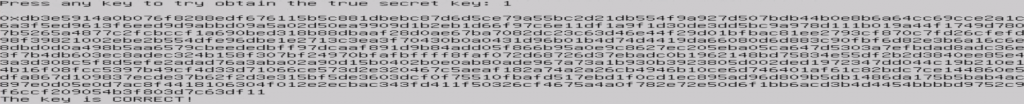
As part of the project the BGU team has implemented a fully-operational cache side-channel attack targeting TLS server authentication, and more specifically recovering the private RSA key used by the server as part of the TLS protocol.
Figure: A snapshot of the attack succeeding in recovering a private RSA key.
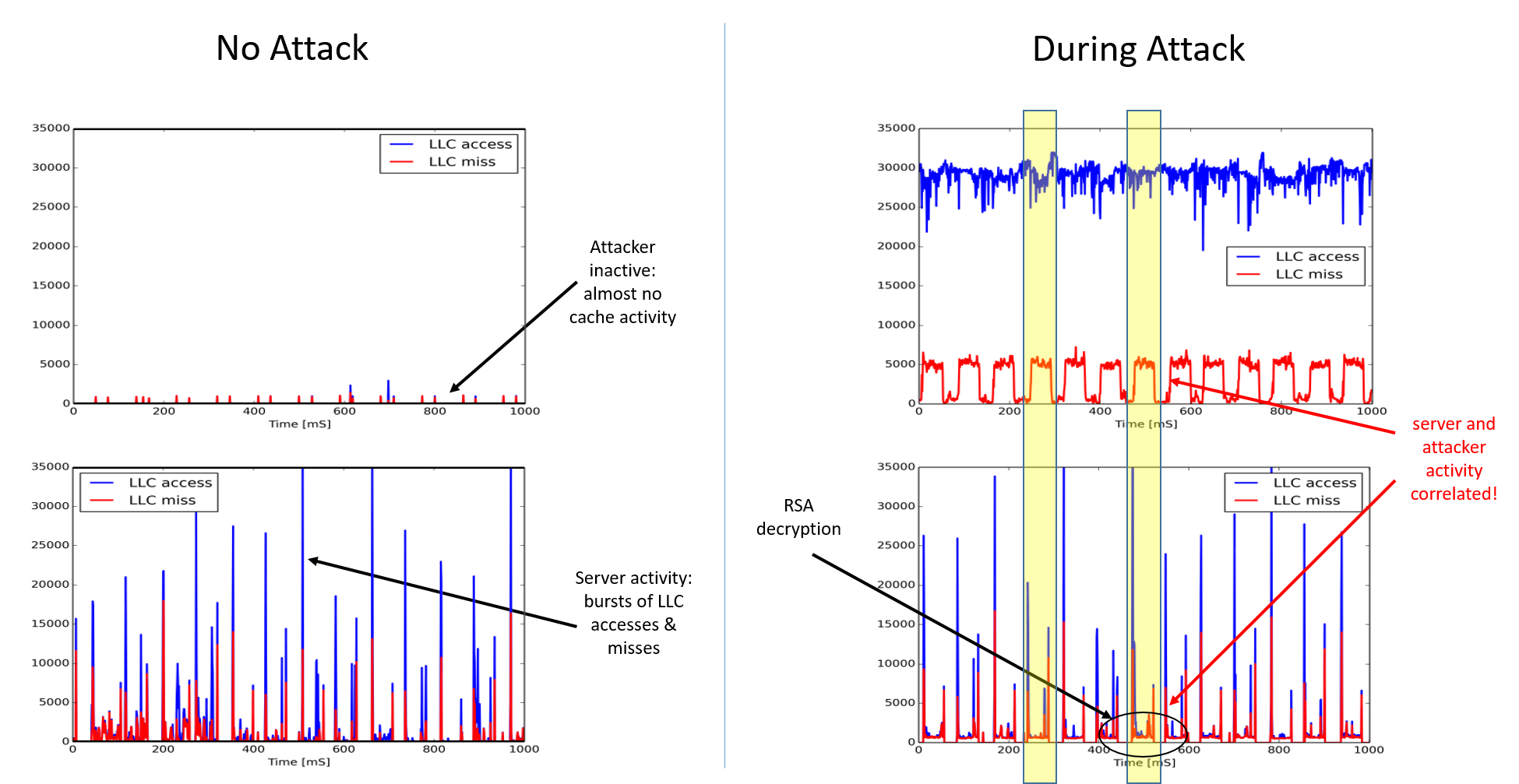
We have implemented a monitoring module that is able to detect an ongoing attack. The module is based on examining several HW counters related to cache activity.
Figure: Cache activity (access/miss) with no attack, and during an attack. Top figure shows attacker VM’s performance, and bottom figure shows target VMs performance.
Furthermore, we have implemented a prototype noisification (is that a word??) module for mitigating the attack. Our experiments currently show that our approach is able to reduce the success rate of an attack from 100% (without any mitigation) within 1 hour to 1.3% within 1 hour (with our mitigation module active).
Achievements and Results
Currently, MIKELANGELO has implemented an LLC side-channel attack able to recover a co-located target’s private RSA key within minutes. We’re sorry(?) we are unable to make the code for this attack publicly available (would you want it to be??)
On the positive side, we have also designed and implemented a monitoring module and noisification mitigation module as part of SCAM, which are able to detect an attack, and baffle an attacker trying to extract information from the cache side-channel.
MIKELANGELO Resources
Reports
- D2.13 The first sKVM hypervisor architecture - published September 2015, introducing the initial sKVM hypervisor architectures, incorporating the IOcm module for optimizing IO performance, the lightweight virtual RDMA module for improved inter-VM communications, and SCAM — our suggested security suite for the hypervisor.
- D3.4 sKVM Security Concepts – First Version - published January 2016, introducing the details of our implementation of the LLC side-channel attack, along with further details of the planned mitigation techniques to be developed within MIKELANGELO.
- D3.2 Intermediate Super KVM - Fast virtual I/O hypervisor – published December 2016, introducing the details of the current implementation of sKVM, and in particular provides a thorough description of the monitoring module and noisification mitigation module, as well as additional future plans for SCAM.
- D2.21 The final MIKELANGELO architecture – published June 2017, presenting the final overall MIKELANGELO architecture, including the detailed description of the the SCAM modules.
Blog posts
- Securing co-location: Job opening at BGU, Israel - Published in October 2015, announcing the opening of a postdoctoral research position to focus on the development of hypervisor-level security modules against cache side-channel attacks.
Software releases
- SCAM module